The Long Awaited Osmocom-BB Tutorial (Part 1): GSM Security Research (Without The Expensive SDR!)
Regular viewers of my channel will know that I am a huge fan of the Osmocom-BB toolset. In this video, I thought I would throw together a tutorial video on how exactly Osmocom-BB is used in the context of hobbyist GSM security research.
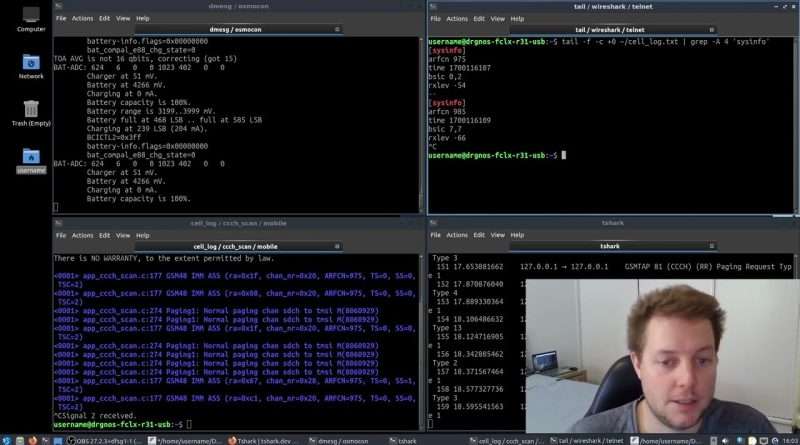
In part one, I list all the hardware and software requirements to work with this software suite. Then, I proceed showcase how Osmocom-BB can be utilized to scan for GSM base transceiver stations (cell towers) in the local area. Next, I show my viewers how the control channel of a 2G cell tower can be decoded and the data viewed in Wireshark. Finally, I demonstrate the usage of the ‘mobile’ application, which allows telephone calls to be initiated and SMS messages to be send from the command line interface.
Part two of this video series will cover the usage of the GSM-sniffing variant of Osmocom-BB, called ‘burst_ind’. Stay tuned for that in the coming days. In the meantime, go and checkout my other videos on the subject in this playlist: https://www.youtube.com/playlist?list=PLqjhBzfQS7YL-vLIaXmD0-wGN5m8uhJwp
This video (and channel) wouldn’t be possible without the amazing Linux distribution, DragonOS FocalX. Friend of the channel, Aaron from the @cemaxecuter7783 YouTube channel works far too hard to provide this incredible Linux distro for us, free of charge. So please, go and subscribe to his channel, like his videos and follow him on Twitter/X!
Thanks for reading and watching!
HARDWARE:
– Core i5 4th Gen PC
– Motorola C117 Mobile Phone
– Sysmocom Serial Cable
SOFTWARE:
– DragonOS FocalX R31
– Osmocom-BB
– Wireshark
– TShark (Optional)
COMMANDS:
– Check if your serial cable is detected by Linux:
sudo dmesg | grep tty
– Upload firmware to calypso phone:
sudo /usr/src/Osmocom-BB/Bin/osmocon -s /tmp/osmocom_l2 -m c123xor -p /dev/ttyUSB0 -c /usr/src/Osmocom-BB/Firmware/e88/layer1.highram.bin
– Initiate ‘cell_log’ application:
sudo /usr/src/Osmocom-BB/Bin/cell_log -i 127.0.0.1 -s /tmp/osmocom_l2 -l cell_log.txt
– ‘Tail’ command to view GSM base station scan:
sudo /usr/src/Osmocom-BB/Bin/cell_log -i 127.0.0.1 -s /tmp/osmocom_l2 -l cell_log.txt
– Initiate ‘ccch_scan’ application:
sudo /usr/src/Osmocom-BB/Bin/ccch_scan -i 127.0.0.1 -s /tmp/osmocom_l2 -a 975
– Launch ‘wireshark’:
sudo wireshark -k -Y ‘!icmp && gsmtap’ -i lo
– Launch ‘tshark’:
sudo tshark -Y ‘!icmp && gsmtap’ -i lo
– Initiate ‘mobile’ application:
sudo /usr/src/Osmocom-BB/Bin/mobile -i 127.0.0.1 -c /usr/src/Osmocom-BB/Config/mobile.cfg
– Login to telnet interface:
telnet 127.0.0.1 4247
– Enable calypso phone radio hardware for ‘mobile’ application:
en
conf t
ms 1
no shut
write
exit
exit
– ‘Mobile’ application telnet commands:
list
show ms 1
show sub 1
show cell 1
sms 1 0062942 Hello, from Osmocom-BB!
call 1 0062942
call 1 hangup
call 1 answer
sim remove 1
sim reader 1
A (VERY STRONG) DISCLAIMER:
THIS VIDEO WAS MADE FOR THE PURPOSES OF EDUCATION AND EXPERIMENTATION ONLY. IMSI-CATCHING, SMS-SNIFFING AND VOICE CALL INTERCEPTION ON CELLULAR NETWORKS IS ILLEGAL AND PUNISHABLE BY HEFTY FINES AND IMPRISONMENT!
Views : 281
GSM