Passive IMSI Catching On A Real GSM Network Using A RTL-SDR And Gr-GSM
Recently, I had the opportunity to play around with a real 2G cellular network. So, here is a quick video of how passive IMSI catchers are constructed using a couple of Linux software tools and an RTL-SDR dongle.
It is a common misconception that mobile phones are tracked via their telephone numbers or the IMEI number of the handset. IMSI is an abbreviation that stands for ‘international mobile subscriber identity’ and is the unique identifier of a mobile phone subscribers SIM card on a cellular network. IMSI numbers are used in most mobile phone communication generations from 2G, all the way up until the more modern 5G.
The IMSI number of a SIM card is very well protected in 3G, 4G and 5G. However, in the case of the 2G mobile communication standard GSM, these unique identifying values are not so well protected from the prying eyes of governments, militaries, law enforcement and spy agencies.
If the IMSI number of a surveillance target/victim is known, it can be used to track and monitor movements of a mobile subscriber.
Typically, an IMSI-catcher is some form of ‘active’ device, performing a man-in-the-middle, false base-station attack to fool the victims 2G mobile phone into thinking it is connecting to a legitimate GSM cell. These devices are called a « StingRay » and are deployed by police, spies and soldiers for the purposes of tracking and surveillance of a target.
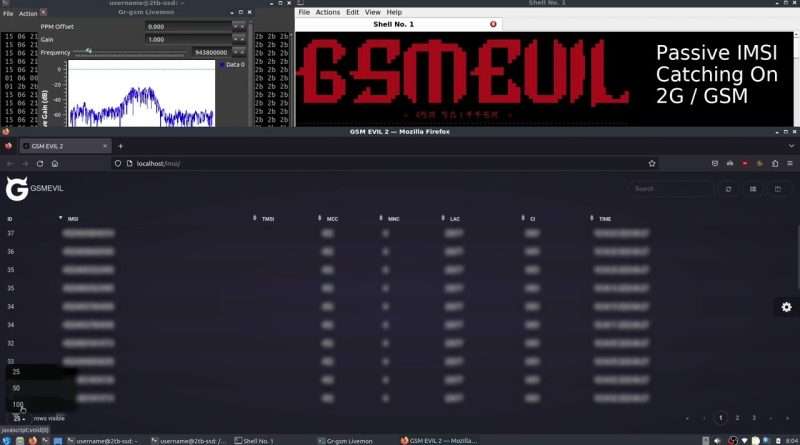
In order to show viewers of my channel how insecure 2G GSM is, I have constructed a ‘passive’-type IMSI catcher using DragonOS Linux, an RTL-SDR dongle, Simple-IMSI-Catcher script and GSMEvil2.
Passive IMSI-Catchers are distinct from StingRay’s because they are ‘receive-only’ and collect mobile subscriber IMSI values that are being sent over the control channel of a 2G base station, whereas a commercial StingRay products sit in between the 2G base-station and the victims mobile phone, and are therefore required to transmit data.
In the first half of the video I am showcasing ‘Simple-IMSI-Catcher’ which is the python script running in the bottom terminal window. In the final half of the video, I am using GSMEvil2 which has a nice web interface/GUI. The sniffed IMSI data is blurred out for obvious reasons. Oh, and please don’t try this at home!
Thanks for reading and watching!
A (VERY STRONG) DISCLAIMER:
THIS VIDEO WAS MADE FOR THE PURPOSES OF EDUCATION AND EXPERIMENTATION ONLY. IMSI-CATCHING, SMS-SNIFFING AND VOICE CALL INTERCEPTION ON CELLULAR NETWORKS IS ILLEGAL AND PUNISHABLE BY HEFTY FINES AND IMPRISONMENT! YOU HAVE BEEN WARNED!
Views : 1811
GSM