Cybersecurity Awareness Month – Day 28/31 – Defense in Depth – Detection
Cybersecurity Awareness Month Tip 28/31: Defense In Depth – Compromise Detection
Eventually, most businesses will be compromised. It is a statistical fact. And according to IBM, the average time it takes to detect a compromise is over 250 days. That is more than 8 months of a bad guy being on your network without you knowing.
When we talk about defense in depth, it is important to acknowledge that defenses are not absolutes. Even if a defense « fails » it may still help slow attackers down, leave forensic evidence for investigators to follow, or set off an alarm so you know you are under attack.
And that is what today’s tip is about, ensuring you have visibility into the bad stuff. A common part of host base defenses are around simply knowing if bad stuff is happening, even if you can’t automatically stop it.
The D in EDR, XDR, and MDR standards for Detection becasue these tools help you understand if a host is compromised.
A NIDS is a Network Intrusion Detection System that watches traffic on things like routers or switches to determine if the activity is suspicious.
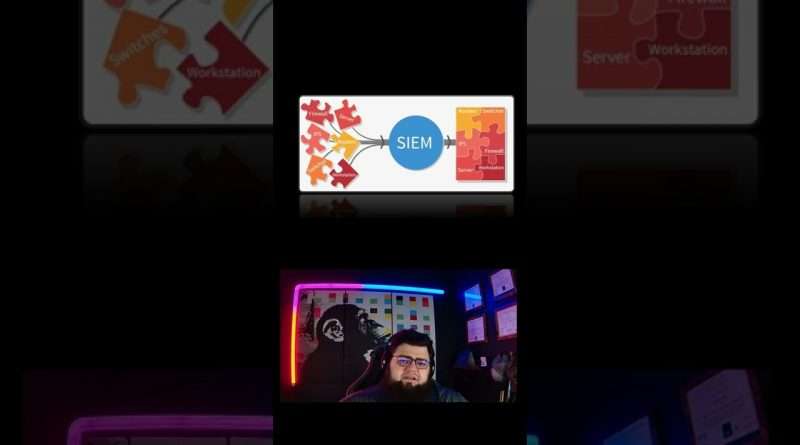
In an ideal world, all of this data is fed into a SIEM (Security Information and Event Monitoring) tool, and monitored by a SOC or IT team who understands what to do with the information.
Using frameworks like the MITRE ATT&CK Defender SOC Evaluation to help you better understand your collection capability and your blind spots is a great way to help ensure that your detection capability is keeping up with your defenses.
#cybersecurity #blueteam #infosec #killchain
https://www.linkedin.com/posts/jordansilva_cybersecurity-blueteam-infosec-activity-6993101803533848576-UaQk?
Views : 2
cyber security