Biological Viruses vs Computer Viruses | Security Confidential
#SecurityConfidential #darkrhinosecurity
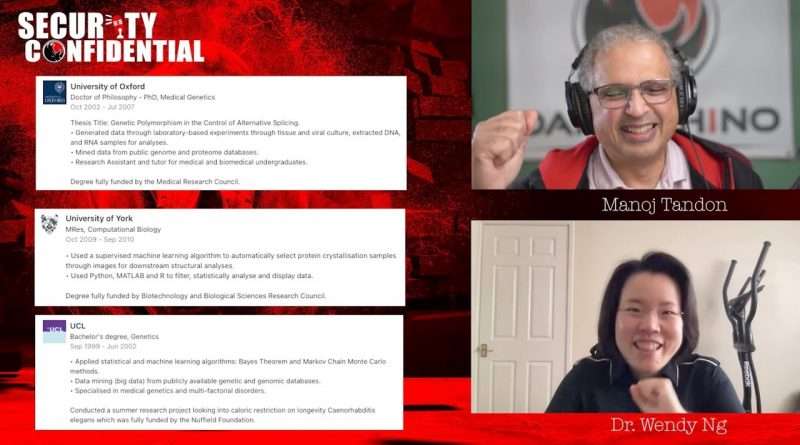
Wendy is a keynote speaker, Principal Cloud Security Architect, and senior security advisor. She has worked for Cisco, PWC, and Deloitte. Has a doctorate from the University of Oxford. She is currently with OneWeb. Prior to joining OneWeb, Wendy was Experian’s DevSecOps Security Managing Adviser and defined the strategy for the organization’s global DevSecOps transformation initiative. Wendy is active in the community, regularly sharing experiences through keynotes, Blogs, and Black Hat.
00:00 Introduction
00:21 Our Guest
01:40 Transitioning from Medical Genetics to Cyber
04:50 The importance of having people from different fields
07:41 Comparisons between Biological Virus and Breach
12:09 Low Earth Orbit Constellation
18:18 Hackers are Collaborative
22:01 100% Security
26:30 Understanding the Risk
30:40 Building a Culture of Awareness
35:35 DevSecOps
38:50 Controlling that 3rd party risk
43:15 Connecting with Wendy
To learn more about Dark Rhino Security visit https://www.darkrhinosecurity.com
———————————————————————-
SOCIAL MEDIA:
Stay connected with us on our social media pages where we’ll give you snippets, alerts for new podcasts, and even behind the scenes of our studio!
Instagram: @securityconfidential and @OfficialDarkRhinoSecurity
Facebook: @Dark-Rhino-Security-Inc
Twitter: @darkrhinosec
LinkedIn: @dark-rhino-security
Youtube: @Dark Rhino Security
———————————————————————-
Articles Mentioned:
https://hubsecurity.com/blog/our-events/zero-trust-speaker-spotlight-with-wendy/
https://medium.com/epic-women-in-cyber/epic-women-in-cyber-dr-wendy-ng-70308ade5615
https://www.inspiredbusinessmedia.com/speaking-with-onewebs-wendy-ng/
https://www.linkedin.com/pulse/black-hat-mea-cyber-considerations-leo-constellations-dr-wendy/
https://cyber-security.degree/resources/history-of-cyber-security/
Cyber-Attack Dwell Time: How Low Can You Go (Before It Really Helps)?
https://www.avast.com/c-hacker-types#:~:text=White%20hat%20hackers%20probe%20cybersecurity,re%20not%20always%20ethical%20either.
———————————————————————-
Views : 20
cyber security