Finding GSM (2G) Voice Call And SMS Encryption Keys: Cracking The A5/1 Cipher With Kraken!
A5/1 is a encryption algorithm developed in 1987 to provide secure communications over the GSM (2G) mobile telephone standard. Until the widespread adoption of A5/3 (KASUMI), it was considered to be the strongest form of encryption provided by the A5 family of security protocols.
To my (very limited) understanding of how GSM security works, when private user data is about to be transmitted or received (e.g. voice call or SMS message from a cellular network subscribers telephone) an authentication request is sent by the base station (tower). If the users mobile phone responds in the correct way expected by the base station, a 64-bit ‘session key’ (commonly known as the ‘Kc’ value) is generated by the telephones SIM card and the base station tower independently. If these values match, the authentication is successful and encrypted communications can commence.
Obtaining the ‘Kc’ value is easy if you have an older GSM phone such as a Blackberry, or an early iPhone or Samsung. SIM card readers can also obtain this value, as can Osmocom-bb. All of these methods make reading your own SMS messages and listening to your own voice calls easy with tools such as Airprobe and gr-gsm.
If the ‘Kc’ encryption key isn’t previously known, and some A5/1 secured GSM data has been captured via software defined radio, the process of obtaining the secret key is called ‘cracking’.
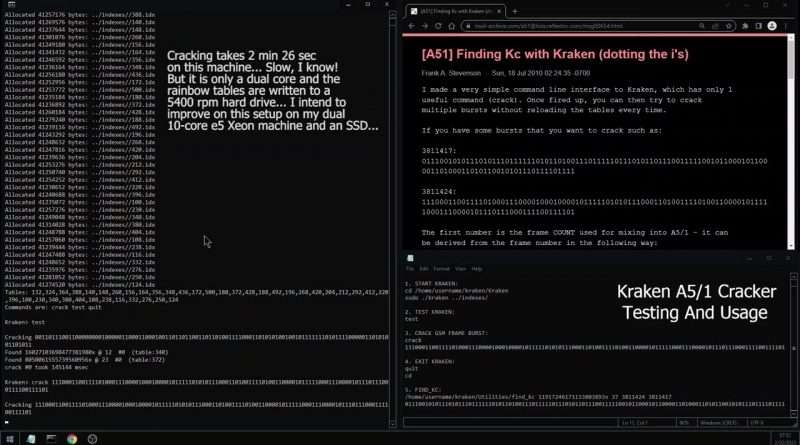
Kraken is a piece of free open-source software developed in 2009 and publicly announced in 2010. It enables a type of time/memory/data tradeoff attack using 1.5 Terabytes of pre-computed « rainbow tables » and can be used to obtain the 64-bit encryption key. It is a very technical and involved process and vast knowledge of cryptography and GSM authentication must be known before trying to attempt this.
In this video, I am following instructions posted in the A5/1 mailing list by Frank, the author of Kraken. Using a sample GSM ‘burst’, I show how it possible to retrieve the 64-bit secret key.
The PC I am running the A5/1 cracking tools on is a very old dual core i3 H61 machine and the hard drive containing the rainbow tables is a NAS 5400 rpm SATA HDD. Not the most optimal setup as you can see, since it requires more than two minutes to ‘crack’ the key. With modern PC’s, it’s possible to reduce this time to a minute or less. Thanks for reading and watching!
LINKS:
Kraken Tutorial:
https://web.archive.org/web/20141227210334/https://lists.srlabs.de/pipermail/a51/2010-july/000688.html
Kraken GitHub:
https://github.com/0xh4di/kraken
COMMANDS:
1. START KRAKEN:
cd /home/username/kraken/Kraken
sudo ./kraken ../indexes/
2. TEST KRAKEN:
test
3. CRACK GSM FRAME BURST:
crack 111000110011110100011100001000100001011111010101110001101001111010011000010111110001110000101110111000111100111101
4. EXIT KRAKEN:
quit
cd
5. FIND_KC:
/home/username/kraken/Utilities/find_kc 11917246171133803893x 37 3811424 3811417 011100101011101011101111110101101001110111110111010110111001111100101100010110000110100011010110010101110111101111
Views : 45
GSM